Almost unbelievably, 91 percent of all health organizations have reported a breach of protected healthcare information over the last two years. By extension, mobile health (mHealth) apps are among the most difficult apps to develop owing in part to their need for HIPAA Compliance. They must comply with the Health Insurance Portability and Accountability Act (HIPAA) of 1996.
HIPAA or Public Law 104-191 comprises 168 pages of absolutely riveting reading. To spare you some of the pain, we’ll address HIPAA compliance essentials for mHealth apps and the Internet of Medical Things. HIPAA falls under the purview of the US Department of Health and Human Services (HHS). If you are looking to develop a medical app, you may also wish to examine US Food and Drug Administration , as well as Federal Trade Commission requirements.
HIPAA’s Purpose?
HIPAA was enacted to set national standards for the:
- Protection of privacy of health information,
- Security of electronic records,
- Administrative simplification,
- Insurance portability.
Breaches of protected healthcare information can put lives at risk. That alone is good enough reason to comply with HIPAA. Generally, civil suits are not brought forward for HIPAA violations, but that’s not sacrosanct per rulings in the State of Connecticut. Regardless, civil suits can be brought forward for violations of state and/or federal law. HIPAA compliance reduces healthcare provider exposure to civil suits by helping prevent threats to protected healthcare information in the first place.
HIPAA Compliance Overview
HIPAA was enacted to set national standards for the protection of private health information, the security of electronic records, administrative simplification, and insurance portability. There are four rules associated with HIPAA Compliance, some involving important distinctions:
- Privacy Rule – covers protected healthcare information (PHI).
- Inclusion of personally identifiable information (PII)
- Identification of “covered entities and business associates.”
- Difference between data de-identification and anonymized data.
- Security Rule – involves administrative, physical and technical safeguards.
- Risk assessment
- Administrative safeguards
- Physical safeguards
- Technical safeguards
- Breach Notification Rule – protocols in the event of a security failure.
- Enforcement Rule – potential civil and criminal penalties.
As with all legalese, definitions and source data can be very important. Wherever possible, we include links to source documents. The Privacy Rule deserves extra attention, as it defines whether you will need to achieve HIPAA Compliance, what data is covered, and (very limited) exceptions of how otherwise protected data can be used. Likewise, a large volume of materials and guidance are available for each of the respective safeguards.
The HIPAA Privacy Rule
Protected Health Information (PHI) under HIPAA’s Privacy Rule protects all past, present and future “individually identifiable health information held or transmitted by a covered entity or its business associate, in any form or media, whether electronic, paper, or oral.”
PHI specifically includes all items listed in the first column in the table below. However, it also includes any personally identifiable information (PII).
| PHI | PII | & More PII |
|
|
|
You may also see ePHI used to designate Electronic Protected Health Information. Essentially that encompasses any of the data above that is created, stored, transmitted or received electronically – via any electronic device or storage medium.
For the sake of a little humor, there are no loopholes without getting all sci-fi with telepathy. But, even that can be argued as requiring electronic devices. What constitutes sci-fi today may not be tomorrow.
HIPAA Compliance – Are you a covered entity?
If you are a covered entity or a business partner of a covered entity you are required to be HIPAA compliant. Determining whether you are a “covered entity” is almost as easy, depending on what your definition of is, is. Essentially, if you or your business is involved with handling healthcare information, or you are a business associate of someone who is, you are quite likely a covered entity. Here’s a more detailed checklist to help you answer the question line by line because there are always exceptions.
De-Identified Data vs. Anonymized Data
Anonymized Data irrevocably removes and disconnects all PHI/PII associated with a data contributor. De-Identified Data is similar except there are some situations where the data may be relinked to a data contributor, per 45 C.F.R. §§ 164.502(d)(2), 164.514(a) and (b). De-identified data often involves limited data sets used for purposes of public health and research.
HIPAA Risk Assessment and Security Rule
HIPAA’s Security Rule requires covered entities and their business associates to conduct a risk assessment of their healthcare organization. The goal of this assessment is to help keep your business compliant with HIPAA’s administrative, physical and technical safeguards. These are likely to apply to any mHealth or IoMT app you may develop to help you identify vulnerabilities associated with your handling of PHI. A risk assessment tool and additional risk analysis guidance are provided on the HHS website.
The Security Rule requires the implementation of three layers of safeguards – administrative, physical and technical. The goal is for all three to be integrated as one coherent program, suffice that aspects of each layer can easily overlap with others. The three layers are delineated below along with links to the established standards for each.
- Administrative security – relating to the security management process, assigned security responsibility, workforce security, information access management, security awareness and training, security incident procedures, contingency planning, program evaluation, business associate contracts, and other arrangements.
- Physical security – required to protect electronic systems, equipment, and data including facility access controls, workstation use, workstation security, device and media controls.
- Technical security – authentication & encryption used to control access to data, audit controls, integrity, and transmission security.
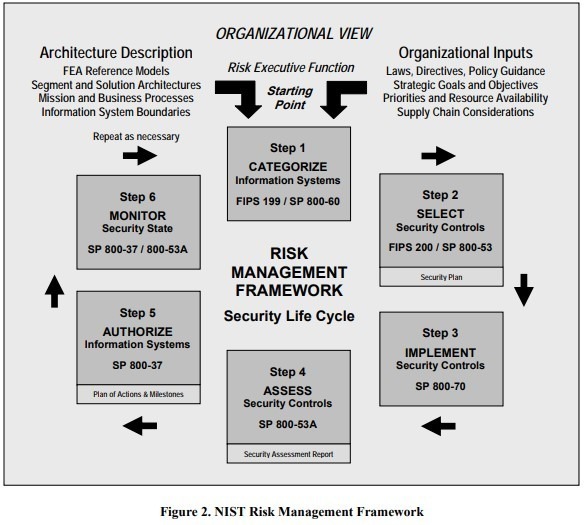
To further assist covered entities, the HHS Office for Civil Rights and the National Institute of Standards and Technology (NIST) have provided a “Crosswalk PDF.” This document helps correlate the NIST Framework for Improving Critical Infrastructure Cybersecurity (aka the Cybersecurity Framework) with the HIPAA Security Rule and other security frameworks. This is not required by HIPAA, but serves to promote all covered entities and their business associates to enhance their cybersecurity programs.
Breach Notification Rule
The HIPAA Breach Notification Rule defines reporting requirements, exceptions and provisions in detail. In the event of a breach, a covered entity must notify any individuals whose PHI has been compromised, the media for cases involving more than 500 people’s records, and the Secretary of Health and Human Services. The legalese is covered in 45 CFR § 164.400-414. However, “Similar breach notification provisions implemented and enforced by the Federal Trade Commission (FTC), apply to vendors of personal health records and their third party service providers, pursuant to section 13407 of the HITECH Act.”
HIPAA Enforcement Rule
The HIPAA Enforcement Rule – PDF contains provisions relating to compliance and investigations.
Fines for non-compliance start at $10 but can run up to $50,000 per violation or individual record, but with a maximum penalty of $1.5 million per year. There are different tiers of penalties. Intentional HIPAA violations carry criminal penalties of $50,000 – $250,000 and up to a year in jail. Accessing or distributing PHI under false pretenses can result in a 5-year sentence. Doing so with malicious intent or personal gain pushes that to 10 years.
Last year (2018), the Office for Civil Rights (OCR) at the U.S. Department of Health and Human Services set its all-time record of $28.7 million for HIPAA enforcement. Their overview of enforcement results indicates that they’ve referred over 700 cases to the Department of Justice for criminal investigation involving the improper handling of PHI.
Top Five Issues in Investigated Cases Closed with Corrective Action, by Year
| Year | Issue 1 | Issue 2 | Issue 3 | Issue 4 | Issue 5 |
| 2017 | Impermissible Uses & Disclosures | Safeguards | Administrative Safeguards | Access | Technical Safeguards |
| 2016 | Access | Impermissible Uses & Disclosures | Safeguards | Administrative Safeguards | Technical Safeguards |
| 2015 | Impermissible Uses & Disclosures | Safeguards | Administrative Safeguards | Access | Technical Safeguards |
| 2014 | Impermissible Uses & Disclosures | Safeguards | Administrative Safeguards | Access | Technical Safeguards |
Volume of HIPAA Breaches
In the 24 months leading up to February 2019, HHS reported 433 major breaches of Protected Healthcare Information. That’s up from 364 breaches in the same time frame leading up to September of 2017. This involves breaches associated with all causes (hackers, unauthorized access, misconfigurations, etc), that impacted more than 500 people. Hacking remains the #1 cause of PHI breaches. Cumulatively, they impacted of over 15 million people in each reporting period. This does include the recent database misconfiguration at UW Medicine, which affected nearly 1 million individuals.
HIPAA Certification, Audits, and Compliance
One myth that we can get out of the way is any need for “HIPAA Certification.” Different organizations may offer classes and training that lead to “HIPAA Certification” but they are not an official or legally recognized form of accreditation.
HIPAA Audits, however, are real and may be conducted on any covered entity or business associate. More details are also available, including an FAQ that explains everything about audits in detail. Independent audits can run in excess of $20,000. They are not required but can be useful in identifying any shortcomings your organization may have in achieving compliance.
The HIPAA Journal provides one of the most comprehensive and easy to follow HIPAA Compliance Checklists available for covering all the interests of a covered entity or business associate. There are no requirements for businesses to pay for or conduct independent audits which can run over $100,000 depending on their thoroughness.
FTC and FDA Resources
If you are developing a mobile application, you will also need to comply with federal laws subject to oversight by the US Federal Trade Commission and the Food and Drug Administration. You may be interested in checking out, Does your mobile medical app need FDA approval? We’re sharing our list of essential resources below for quick reference.
- Start with The FTC’s Mobile Health Apps Interactive Tool – Answer their 10 questions and the tool will point you to relevant federal laws and resources relevant to your mobile health app.
- FDA Overview of Mobile Medical Applications – The FDA’s main website.
- FDA Guidance on its Regulation of Mobile Medical Applications (PDF) – Primary document referenced in this article.
- FTC Best Practices for Mobile Health App Data Security – Also useful as it gives you access to the Start with Security: A Guide for Business 20 page PDF.
- Federal Trade Commission Act (PDF) – “Prohibits deceptive or unfair acts or practices in or affecting commerce, including those relating to privacy and data security, and those involving false or misleading claims about apps’ safety or performance.”
- FTC’s Health Breach Notification Rule – Reporting requirements following breaches of personal health records and information.
HIPAA and GDPR – “Data Protection by Design”
The EU’s General Data Protection Regulation (GDPR) hit May 25, 2018. It applies to protect the private data of EU citizens. It applies globally to any business who may have or share private data of EU citizens. GDPR applies similarly in many ways to PHI and PII under HIPAA. We offer GDPR by Design an SaaS solution through our parent company, Provectus. It is based on distributed key management that encrypts Personally Identifiable Information and provides users with complete control over their data. If you are looking for a comprehensive long-term solution to manage all of your sensitive data we’d be happy to discuss how our GDPR by Design and mobile app development could work for you.
Disclaimer: The information contained in this article is for general guidance only. Laws vary widely based on the specific facts. Laws, rules, and regulations also change, so there may be inaccuracies in this post. This article is presented with the understanding that Reinvently and its authors are not engaged in rendering legal advice. This article should not be used or construed as a substitute for advice from a legal professional.







Leave a Reply